Background information
Ninja doesn't currently support native AV monitoring via Windows Security Center, integrated AV packages are monitored but what if you need more?
Creating Fields
- Role Custom Fields are custom fields that are specific to a device role.
- Global Custom Fields are custom fields that are applicable to all devices and/or to a location and/or organisation
When you create your custom field you need to make sure that you set the Scripts permission to ensure that you can read or write to the field from your scripts - as appropriate for the script you're using.
We're going to create one role custom field for devices with the Windows Desktop or Windows Laptop role:
| Field Name | Field Type | Description |
|---|---|---|
| Detailed AV Status | Multi-Line | Output for each configured AV on the system including name and status information. |
The Script
This script won't work on Windows Server operating systems as they lack a CIM or WMI interface to the Windows Security Center which allows us to easily programmatically query the AV status.
loading...
Monitoring
The script includes support for two monitors.
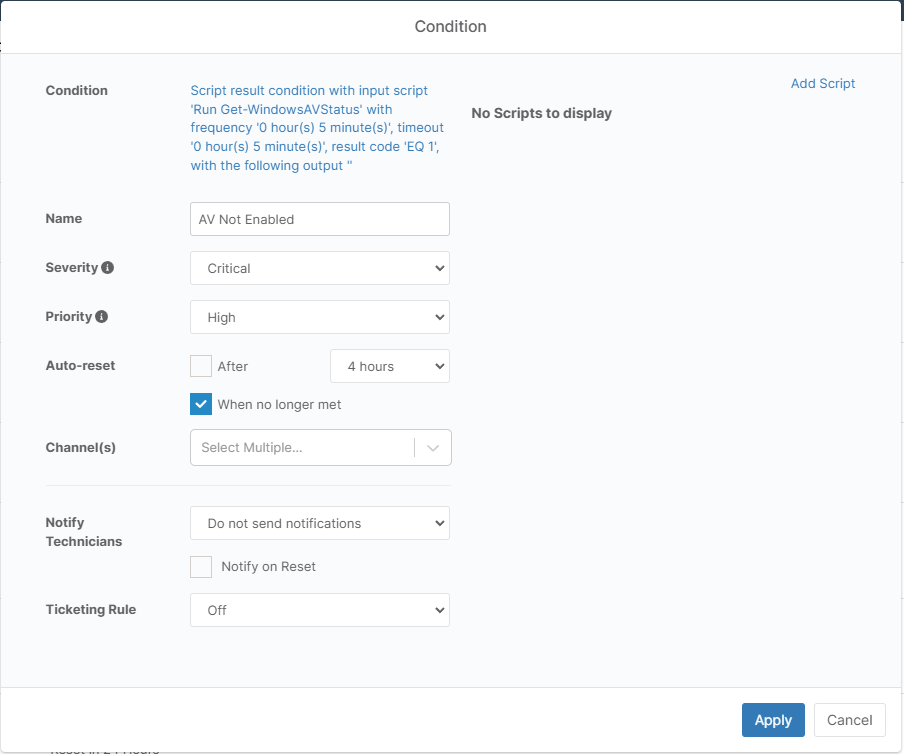
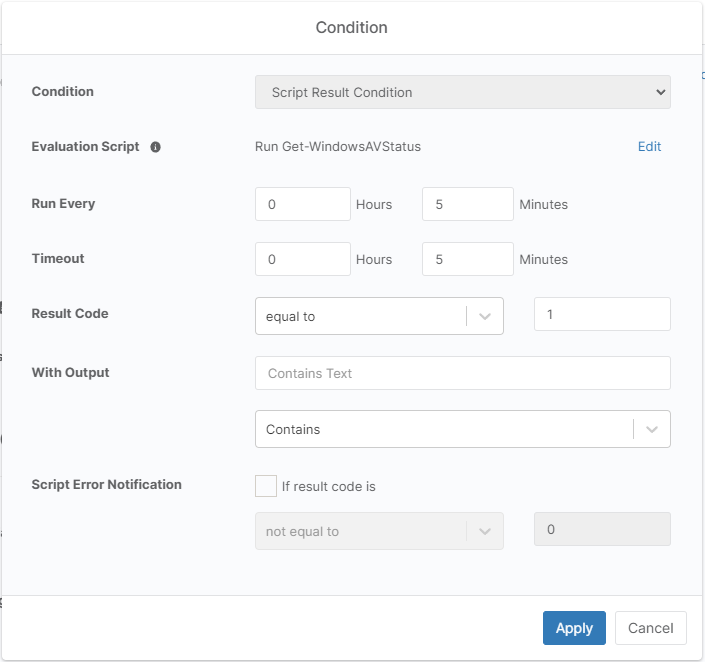
AV Not Enabled
Setup a script result condition monitor that runs this script with a check for an exit code of 1.
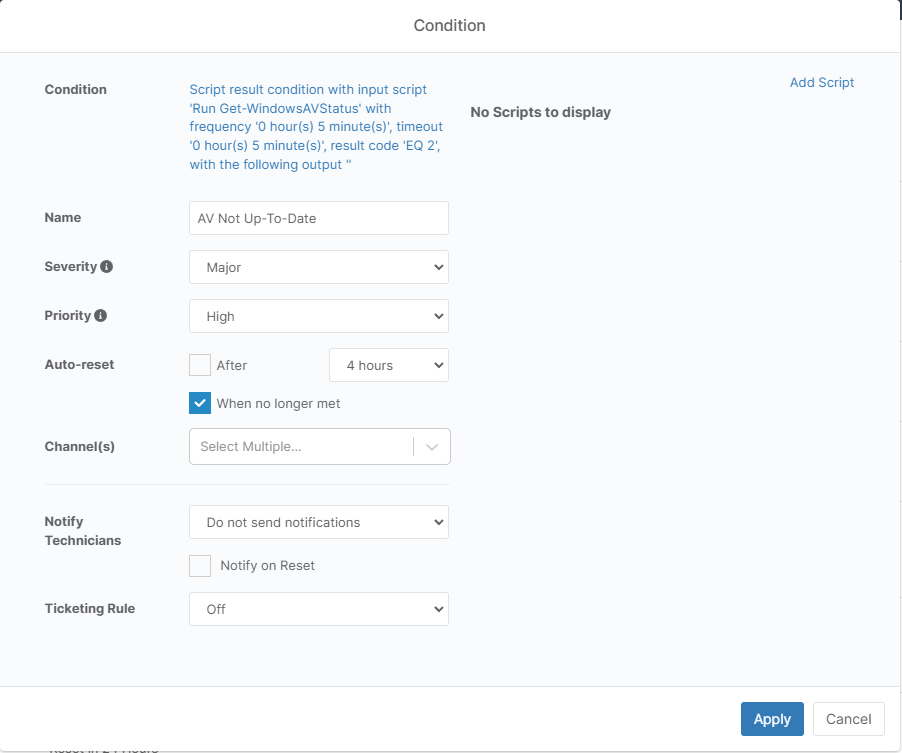
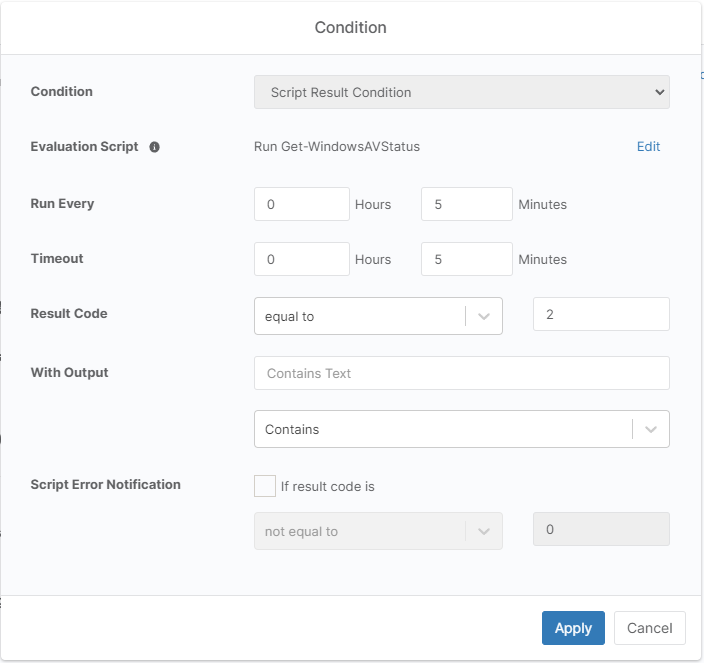
AV Not Up-To-Date
Setup a second script result condition monitor that runs this script with a check for an exit code of 2.